What is Threat Hunting?
Threat Hunting means to proactively search for malware or attackers that are hiding in your network — and may have been there for some time.
What is the Goal of an Attacker?
Most time, the goals of these malware or attackers can be to quietly stealing off data, patiently listening in for confidential information, or working their way through the network looking for credentials powerful enough to steal key information.
And at the same time, they might be there to harness your computing resources for use in the Botnet army under the control of a C&C(Command and Control).
Many organization servers are been used to launch coordinated bot attacks such as DDOS (Distributed Denial of Service) across the world while such organizations, incur the cost of processing power, electricity, maintenance etc.
Why is Threat Hunting Important?
When the traditional protections we have in an organization fails to detect Advanced Persistent Threat (APT) , then threat hunting is the only way to help discover them.Basic security hygiene and properly implemented EDR (End Point Detection and response), firewalls and other automated security tools should stop the majority of threats from getting in.
Most time, these malware and attackers are able to get into our network through applications we deemed legitimate ( a case study of where one of the legitimate application installed in an organization is initiating a connection to a C&C using one of its background process) .
Once an attacker has sneaked into our network undetected, there’s often not much to stop them from staying there.
According to a research, it takes on an average of 191 days for a cyber criminals (considering all forms of TTPs) to be discovered once they’re on your network.
This is a great long time to cause the havoc they intended, which can undermine business continuity and existence. In contrast to a cyber forensic , which is designed to work out what went wrong after an attack, Threat Hunting aims to track down these waiting attackers and stop them in their tracks before they have the chance to cause real damage.
What Do You Need to Start Threat Hunting?
Having a fairly mature security setup capable of ingesting multiple sources of information and storing it in a way that lets you access it, is key to the success of Threat Hunting. Every organization must as well show commitment and readiness towards it and do well by allocating necessary resources.
How to Run a Successful Threat Hunting In Your Organization
What should be included in the basic setup every organization need to have a successful Threat Hunting are; automated blocking and monitoring tools such as firewalls,IDS/IPS, EDR, network packet capture, and a SIEM(Security Information and event management).
And most importantly,a platform that will give you a step ahead of the attackers needs to be on ground. Provision of access to Threat Intelligence resources so you can look up IP addresses, malware hashes, IOCs, URL reputation, C&C activities, feeds and more.
And also, a tool that allows the organization to bring together all of these disparate data sources and slice and dice them in a way that reveals actionable intelligence with the least possible effort will also be required.
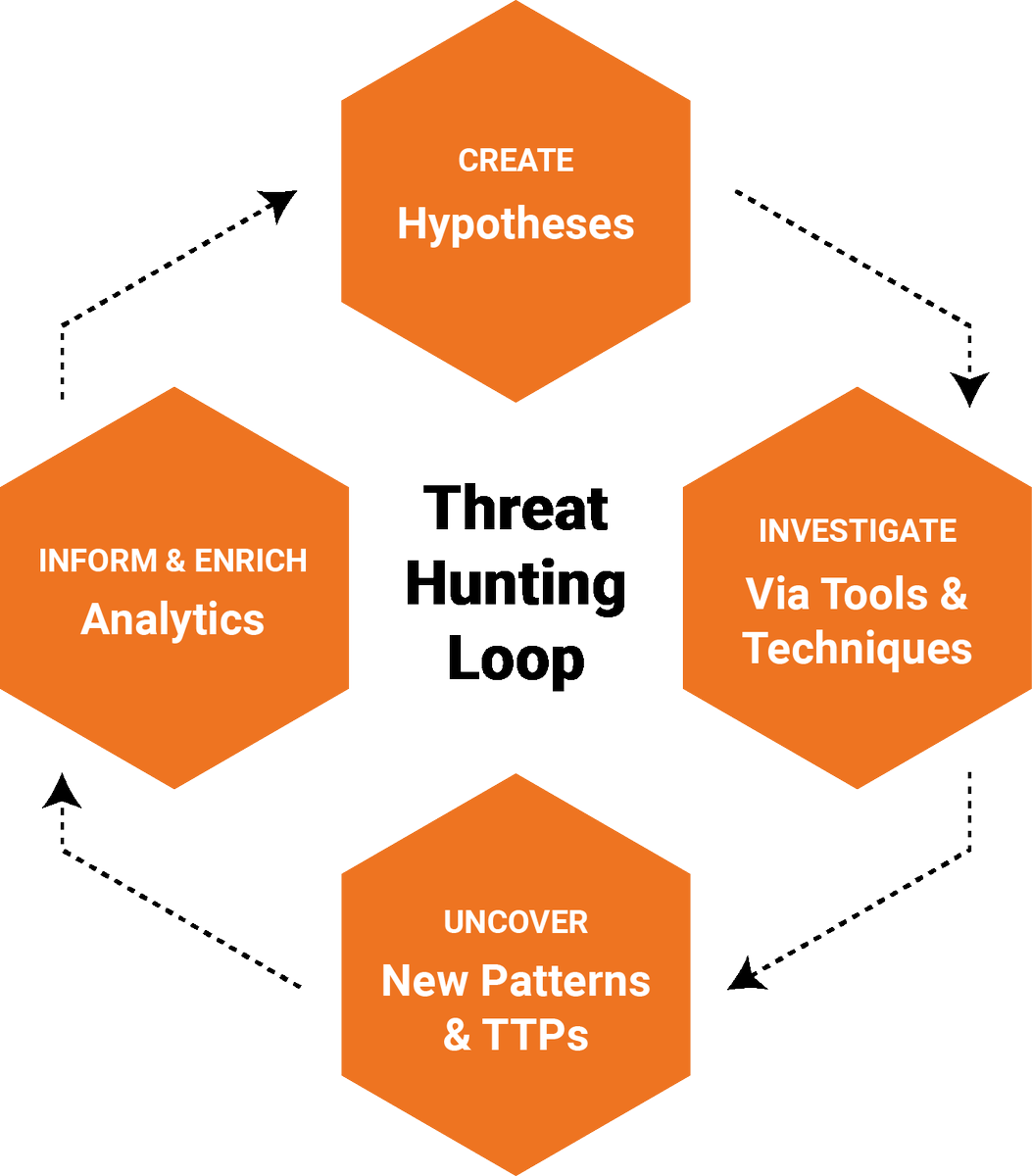
As soon as we can bring all tools in place and working together, the need for a team with enough people and skills to manage the technology and vast amount of data involve is required.
Threat Hunting is an advanced and complex task, but with the right people, technology and questions, it can help re-position your organization’s security posture for the better and prevent major problems before they occur.
Following the Threat Hunting Loop, It is very easy to create a threat hunting procedures that matches the need of your organization.









